Abstract:- For many years and still today, there have been significant risks related to computer systems. The hazards that are covered in this article include judicial, security, and privacy threats. Risk is typically classified as either speculative or non-speculative and is characterized as a function of event likelihood and impact. Taking chances in the hopes of reaping rewards is known as taking on speculative risk. Risk can be evaluated in two major ways: quantitatively and qualitatively. Determining risk exposure consciously is what is meant by risk management. The risk acceptance criteria and a reflection of the hazards that individuals are ready to accept serve as the foundation for the risk management process.
Keywords–Security Aggregation and Dissemination, Software Risk Management, and Network Risk Management
I.INTRODUCTION
Risk Management in Information Security Risk is typically classified as either speculative or non-speculative and is characterized as a function of event likelihood and impact. Taking chances in the hopes of reaping rewards is known as taking on speculative risk. Gambling is a case in point. Risk Management in Information Security You might stake a particular sum and lose. You can still win bets and receive extra incentives, and there are still possible upsides. Risks that are not speculative only have a negative effect.Risk Management in Information Security Natural disasters or computer system flaws, for instance, could have a bad effect on your company. Risk can be evaluated in two major ways: quantitatively and qualitatively. Think about the possibility that the server’s hardware will fail at some point. The provider could give you a number from the testing facility that says the part can function properly for up to X hours. Moreover, historical information regarding the anticipated lifespan of a component might exist. You are able to calculate the likelihood of failure thanks to advanced assurance. Also, the risk can be accurately evaluated if the impact, i.e., the overall cost of replacing a component, can be determined. Risk Management in Information Security The issue with security risks is that it can be challenging to estimate the probability and consequences of an attack. Qualitative techniques can be beneficial. There are numerous methods for calculating risk. Below is a brief explanation of the model to show how the qualitative approach was used. Risk Management in Information Security To evaluate the risks related to software vulnerabilities, Microsoft developed the DREAD (possible damage, repeatability, availability, affected user, discoverability) model. The model’s basic premise is: given a skilled and determined attacker, how challenging is it to locate and exploit a vulnerability, and what are the potential repercussions of doing so? The risk level is calculated by adding the three ratings for each of the five horror aspects of the vulnerability. Microsoft continues to adhere to Dread’s principles despite substantially improving its risk assessment process. This essay concentrates on weaknesses. But, if there are active attackers, this vulnerability could be dangerous. Risk Management in Information Security It’s critical to comprehend the context of a vulnerability in order to completely comprehend the hazards connected to that vulnerability. Researchers may discover flaws in the system without being able to fully evaluate the hazards involved if there are no publicly available documents on the system. Also, the owners of the system think that this vulnerability is impractical and unexploitable. Second, proof-of-concept attacks can be useful in determining the degree of a vulnerability’s related risk. That at least clarifies the context of the vulnerability and adds unarguable facts to the debate.
RISK MANAGEMENT
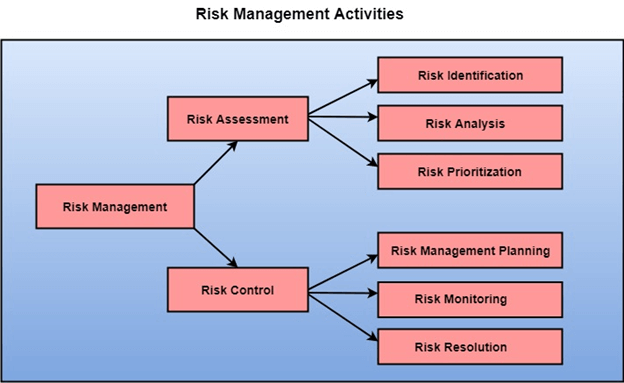
Determining risk exposure consciously is what is meant by risk management. The risk acceptance criteria and a reflection of the hazards that individuals are ready to accept serve as the foundation for the risk management process. Risk assessment and risk management are the two stages of the qualitative risk management process shown in Figure 1. This procedure should be carried out frequently because computer systems and the hazards they pose have a habit of evolving over time. Creating a thorough overview of the system was the first task in the risk assessment phase. Determine risks and vulnerabilities next. The system is at risk as a result of the threats and vulnerabilities present. Lastly, evaluate the risk by figuring out the likelihood and consequences of each danger and vulnerability pair. For the overall risk management process to be successful, a thorough assessment is essential. The second phase determines the risk for the identified risks using risk acceptance criteria. For each sort of risk, there are four ways to go about it.
Accept — No action is necessary because this danger is acceptable.
Control — The risk is too great, but there are steps being taken to lessen its likelihood and effects, and those steps are acceptable.
Reject — Say, for instance, that the risk is too great to be avoided. Avoid hazards or give up risky activities.
Transfer – Through the use of insurance, for instance, risk is transferred to third parties.
There is a residual risk that satisfies the risk acceptance criteria after the risk processing step.
A] Network productivity and security are improved through network risk management.
Organizations must take all reasonable precautions to safeguard the business and the tools employed to do business since client trust is crucial to developing a strong customer base and growth. This includes managing network security by utilizing the Internet and cloud computing to their fullest potential while reducing the risks related to conducting business in an environment susceptible to cyber-attacks, viruses, malware, and hackers.
B] Risk management for software
Risk management has been promoted as a method to assure the success of software projects over the years. This provides benefits for software quality and project completion. Verdon and McGraw view risk management as a crucial step in the software development lifecycle for managing software security. Microsoft modified the software development technique and introduced the Trustworthy Computing Security Development Lifecycle after Bill Gates proposed a “trusted computing” program (SDL). Microsoft provided an overview of SDL and came to the conclusion that SDL considerably increased software security based on earlier findings. Another intriguing finding is that the most successful SDL sub-process, risk management (referred to as threat modeling in this paper), is focused on during the design phase. A vital component of protecting business security is risk management. Prior to the Internet era, risk management was primarily concerned with preventing accidents and natural catastrophes from harming property and other assets. Now, however, businesses must take into account how risk management extends to network security and how it pertains to an increasingly digital world.
C] Management of Network Risk
An organization’s digital assets, such as data held on internal and external servers or in public cloud services, as well as digital information in transit, are targets of network risk management, which aims to identify, evaluate, and control threats to these assets. Cybercriminals will follow technology’s development of new connections between people, places, and things and advance in sophistication, leveraging the numerous access points made available to authorized users to gain access to private data. developed a novel technique in a year (2012 to 2013).
Who Manages the Network Risk?
The chief risk officer (CRO), sometimes known as the chief risk manager (CRMO), the risk manager (RMO), or a managed service provider, is responsible for managing cyber risk for the organization. Several organizations, such as the National Institute of Standards and Technology and ISO, have produced risk management standards to assist these administrators in maintaining cybersecurity and being vigilant. These guidelines assist in identifying threats and vulnerabilities, determining how to reduce the risks involved, and putting risk reduction measures into action.
NETWORK RISKS TO ORGANIZATIONS
The threat posed by hackers and cybercriminals worries a lot of senior managers, but many are unsure of what to do. The expense is significant, and it appears to be difficult to handle the threat because danger comes from many different angles. But, it would be costly to approach these threats as random assaults that can only be stopped after they happen. An average of 1.4 cyberattacks per week target each firm. The length of time it takes to reduce the damage depends on the type of attack. Resolving an attack might require a lot of effort and money. The majority of attacks are, nevertheless, somewhat calibrated and predictable. To steal data and money, cybercriminals frequently employ the same input techniques and comparable assaults. Employee access accounts for 15% of attacks, theft devices for 13%, and systems from other companies in the supply chain for 14%. Spear phishing tactics are being used by huge enterprises to commit an increasing amount of cybercrime. This is the process of acquiring access via an employee’s account, assuming the employee’s identity, and then breaking into the business. Before moving money or data to an external account, a variation on this kind of assault involves posing as a manager or other authorized agency employee. The third kind of assault involves a hacker accessing and keeping information or a website while requesting money in exchange. A website may go offline for hours or days as a result of a denial of service (DOS) assault. You can keep track of and find out about each attack as it develops. This challenge can be met by monitoring cybercrime.
- The Best Way to Handle Risk
As a result, many businesses are thinking about using stop loss procedures to safeguard their assets. But, risk management requires a more in-depth strategy. If you are in danger, your company has the following options:
1] Reduce risk by removing the threat of an assault
2] Lessen the possibility of possible attacks
3] Distribute the risk among many divisions and organizations.
4] Keep dangers in mind and deal with them as they arise.
Cybercrime is accompanied by a number of risks. Starting from a larger viewpoint, risk management should work to bring inventory’s level of risk down to a manageable level. The effort and money spent fighting cybercrime, however, is overwhelming for many businesses and government agencies. As a result, you ought to think about setting goals and finding practical means of reducing risk. Organizations can design their own risk management standards with assistance from the National Institute of Standards and Technology (ISO). It is advised that every business take into account the following management strategies:
Included in the organization’s overall architecture
Complete and unmistakable
Consider risk when making all important choices.
Constant monitoring; systematic and structured, yet prone to human error
Looking at various risk variables and ranking them according to which risk factors are the most dangerous and deserving of control is the key to success for the majority of businesses. Danger considerations include employees losing their mobile devices and hackers breaking into money transfer systems. Establishing a strategy to handle the priority risk is the next stage. While some methods may be managed with training, others call for specialist knowledge and technological assistance. Employee education is a great approach to increase visibility and assure the security of entry points, including WiFi and mobile devices.
ADVANCED RISK MANAGEMENT SOLUTIONS
Cybercrime is a force that can be fought. To create a risk management strategy, there is no need to build a small dam in front of the water wall. Governments and large organizations gain despite the cost. Among these advantages are:
Develop your ability to accurately assess and analyze risk variables.
Address challenges to prevent or stop cybercrime
Study risk management strategies
Work with other organizations to identify, prioritize, and stop threats.
Experience with cybercrime demonstrates that there are numerous efficient methods. Most businesses have access to tools like risk management software, data, and ISO criteria. Risk management software is created by Solar Winds MSP (formerly LOGIC), which aids MSP in creating cyber-crime and preventative IT plans.
ESSENTIALS FOR EFFECTIVE RISK MANAGEMENT
- Regular internal audits: Cybercriminals can target weak points at any time, thus keeping an eye on the organization’s network decreases the likelihood that they will penetrate the system deeply.
- Network segmentation into data and other business functions: When hackers access the system, they look for data nodes and transfer money out of the organizations’ hands. Separation systems help to catch and control criminals more easily.
- Cooperation with other organizations: Because cybercriminals target a variety of businesses and organizations, it’s important to work together to create a community that can detect intrusions, report assaults, and track down the attackers.
PROJECTED TRENDS
Due to the requirement to account for quantities that are intrinsically uncertain or difficult to quantify in present methodologies, risk management is more of an art than a science today. Also, there are other ways to combine the components to create a risk reduction approach. As a result, many diverse approaches are utilized today, although none is clearly superior to others. Companies select a risk management strategy based on their unique requirements. There is room to expand the scientific foundation for risk management and raise estimation accuracy in present methodologies. It would also be helpful to have a means to fairly compare various approaches.
CONCLUSION
Risk management is a continuous activity in information security. Risk management is ultimately a decision-making process, one could argue. The gathering of data for the decision-making process occurs during the risk assessment step. The actual decision-making and implementation of the resulting strategy take place at the risk mitigation stage. The continuous feedback into decision-making is provided by the effectiveness evaluation. Even though there is still room for improvement, risk management serves an important and useful purpose for enterprises. Security is one of many urgent needs that organizations must address, and risk management offers a way to decide and justify allocating scarce resources to security needs.
REFERENCE
1] Idrees S. Kocher, Tanveer A. Zia, Hiroshi Ishii, and Chee-Onn Chow (2013). International Journal of Computer Theory and Engineering, Vol. 5, No. 5, October 2013, “Threat Models and Security Problems in Wireless Sensor Networks”
2] W. Su, Y. Sankarasubramaniam, I. F. Akyildiz, and E. Cayirci (2002). IEEE Communications Journal, vol. 40, no. 8, pp. 102–114, “A survey on sensor networks.”
3] Upasana Bahuguna and Kriti Jain (2012). IJSTM, Vol. 3 Issue 2, pp. 83-90, “Survey on Wireless Sensor Network.”
4] P. S. Krus, B. J. Matt, and D. W. Carman (2000). Network Associates, Inc., Glenwood, MD, “Constraints and techniques for distributed sensor network security,” Technical Report 00-010, NAI Labs.
5] Akyildiz, I.F., and Stuntebeck, E.P. (2006). Ad-Hoc Networks 4, pp. 669–686: “Wireless Underground Sensor Networks: Research Challenges”`

