Dynamic — The security of one’s information while utilizing distributed computing is the subject of this examination. Chances and Answers For Information Security in Distributed computing It is an examination concerning the information put away in the cloud as well as the different issues of information security that are associated with it. In this paper, we will go into the particulars of information assurance strategies and approaches that are used in various regions of the planet to give the most significant level of information security conceivable by limiting expected risks and dangers. The accessibility of information in the cloud is profitable for a wide assortment of uses, however, it likewise presents dangers since it opens information to applications that may as of now contain weaknesses in their security conventions. Along these lines, the usage of virtualization for distributed computing might endanger information when a visitor working framework is run on a hypervisor without first deciding the reliability of the visitor working framework, which might contain a security blemish. Also, the paper will reveal insight into the different aspects of information security that relate to information both while it is on the way and when it is put away. The examination thinks about all parts of Programming as a Help (SaaS), Stage as an Assistance (PaaS), and Framework as a Help (IaaS) (Foundation as a Help).
Keywords—Data Security, Cloud Computing, Data Protection, Privacy, Risks, and threats
Introduction
Chances and Answers For Information Security in Distributed computing is There has been a new rise of the expression “Distributed computing,” however it is as yet not usually utilized. One of the most straightforward definitions is “an organization’s answer for offering modest, trustworthy, open, and basic admittance to IT assets.” The focal point of distributed computing is on the hidden administrations, as opposed to the actual applications. Distributed computing’s administration direction not just brings down the all-out cost of possession and functional costs yet in addition gives clients more command over their frameworks and better general execution. Like the progress from conventional figuring to a unified power supply technique, distributed computing begins from a solitary generator at a power-directing plant. This implies that PC capacity can be used as a product and exchanged like water Web based circulated and virtual machine advancements propelled the idea of distributed computing, which intends to bring down the expense of registering by furnishing customers with low-valued PC administrations and capacity choices. The New York T i m e s.
leased Amazon’s distributed computing capacities to change over 11million stories into electronic archives for clients to investigate, at a complete expense of $ 240, which is fundamentally not exactly the expense of one of the handfuls or maybe many customary other options. Chances and Answers For Information Security in Distributed computing Moreover, the cloud is a profoundly viable, speedy way for a startup to get a good deal on basics like servers, programming, and handling limit development. Tragically, distributed computing has not yet accomplished the sort of business strength that we had expected. With regards to adjusting distributed storage for information, protection and information security are significant worries. It is fundamental for the cloud administration to ensure the secrecy of the information as well similar to claim uprightness and security. To accomplish this objective, various different specialist co-ops are using different strategies and systems, every one of not set in stone by the nature, type, and size of the information. One of the advantages of involving distributed computing is the capacity for a few associations’ information to be imparted to each other. In any case, this advantage all by itself comprises a danger to information. Chances and Answers For Information Security in Distributed computing for Information vaults must be safeguarded to avert any possible. While utilizing the cloud to store information, one of the main inquiries to pose is the decision about whether to utilize a cloud administration given by an outsider or to construct an inner hierarchical cloud. Once in a while, the data is excessively delicate to be put away in a public cloud. This could be the situation with information relating to public safety or exceptionally private data in regards to future items, for instance. The repercussions of uncovering this kind of information on a public cloud can be extreme since this information may be really delicate, and the cloud being referred to can be public. At the point when this happens, it is emphatically prompted that the information be put away utilizing the inward haze of the association. Forcing an on- premises information utilization strategy, this system can be useful during the time spent keeping information secure. In any case, this doesn’t ensure total information security and protection on the grounds that many firms don’t have the fundamental aptitude to apply each of the vital layers of assurance to delicate information. The reason for this paper is to explore the techniques for information security that are at present being used all around the world to defend and safeguard information put away in the cloud. It looks at the potential risks that could happen to information put away in the cloud as well as the arrangements carried out by an assortment of specialist organizations to safeguard information. Development of figuring in the cloud.
LITERATURE REVIEW
- A few sites have been surveyed to procure a comprehension of the essentials of distributed computing and the no problem at all capacity of information on the cloud. This part presents a survey of the significant writing to lay out a reason for looking at the n u m e r o u s f e a t u r e s o f t h e i n f o r m a t i o n s e c u r I t i e s
- The creators, Srinivas, Venkata, and Moiz, offer an extremely supportive prologue to the crucial thoughts of distributed computing. The reason for this article is to explore various significant thoughts by analyzing a few examples of applications that might be made with distributed computing and the manners by which these applications can help emerging nations in acquiring benefits from new types of On the opposite side, Chen and Zhao have discussed the clients’ stresses over moving their information to the cloud. As per Chen and Zhao, worries about information security are one of the essential factors that add to the hesitance of significant organizations to move their information to the cloud. The creators have offered a phenomenal examination of the information security and privacy protection challenges associated with cloud What’s more, they have additionally discussed a portion of the potential cures that are out there for these issues.
- On the other hand, Hu and A. Klein fostered a standard that gets information while it is on the way inside a cloud. To safeguard information while it is being relocated, a norm for encryption has been being talked about. Extra encryption is fundamental for solid security, yet it requires extra computational assets to execute. The benchmark that was introduced in their examination offers a trade off that finds some kind of harmony among security and encryption
- Tjoa, A.M., and Huemer explore the issue of protection by giving the end client more command over their information to increment certainty. Various assaults on distributed computing are examined here, alongside a few expected countermeasures to neutralize these assaults.
- In light of this, Abdelkader and Etriby have proposed an information security model for distributed computing that is established on cloud design. Furthermore, they fabricated programming with an end goal to all the more likely advance the Information Security worldview for distributed computing.
Distributed computing AND Distributed storage Distributed computing essentially offer two assistance models:
- process and capacity. Practically any help that runs in the cloud needs admittance to quick, dependable distributed storage to stay aware of client requests. Since information handling is critical to p r e s e n t d a y P C p l an n, I t m a k e s s e n s e t h a t c l o u d.
- figuring organizations would likewise have to offer some kind of distributed storage administration.
- Multi-tenure, tremendous versatility, flexibility, pay more only as costs arise, and self-provisioning of assets are the essential attributes of distributed computing. There are basically three unmistakable kinds of distributed computing administration models. Programming as a help (SaaS) permits clients to get close enough to programming and applications facilitated by specialist co-ops over the web, while the other two classifications — “framework as an assistance” (IaaS) and “stage as an assistance” (PaaS) — give a virtualized processing climate and online stockpiling, equipment, servers, and systems administration parts. One methodology for conveying distributed computing is the “public cloud,” which is held by a specialist co-op and from which clients can lease or buy admittance to the cloud’s assets or a secretly held or rented cloud foundation
- The third kind of cloud is the “local area cloud,” what works in basically the same manner to a confidential cloud however is divided between a more modest gathering.
- A cloud foundation that joins components of numerous organization types is known as a crossover cloud
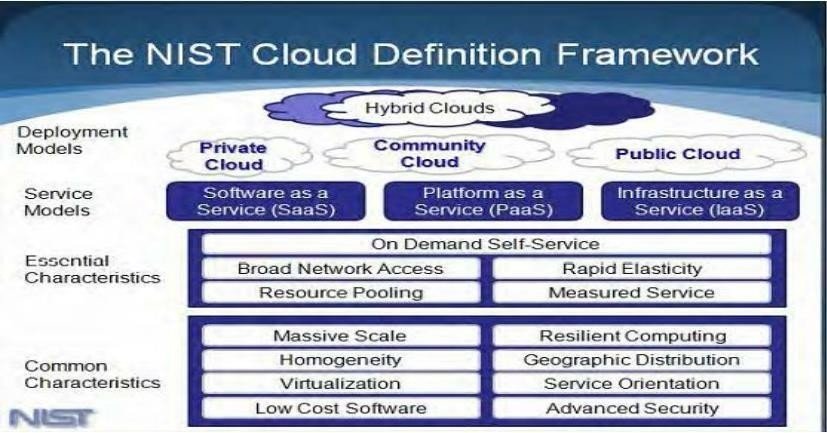
RISKS AND SECURITY CONCERNS IN CLOUD COMPUTING
As talking about takes a chance in distributed computing there are 35 dangers out and out, characterized by ENISA into the accompanying four gatherings: lawful dangers, strategy and hierarchical dangers, mechanical dangers, and general security gambles. The ENISA focused on these dangers by recognizing the main eight. Five of these dangers are explicitly devoted to keeping quiet. Confinement disappointment, information misfortune, dangerous information erasure, malignant insiders, and the executives interface compromise are possible risks. The Cloud Security Coalition (CSA) likewise inventories thirteen particular dangers to cloud administrations. CSA has recognized seven of these dangers as being of the greatest need. Account administration, traffic seizing, uncertain application programming connection points, information misfortune/spillage, and pernicious assaults are five of the seven dangers that all relate somehow or another to information privacy. There are several threats and security issues with cloud computing and its data. The virtualization, public cloud capacity, and multitenancy that are pertinent to distributed computing information security will be the focal point of this exploration.
- Virtualization
All in virtualization, a picture of a completely practical working framework is saved in another working framework with the goal that the genuine working framework can utilize its assets. To run a visitor working framework as a virtual machine in a host working framework, you really want something many refer to as a hypervisor.
Virtualization is one of the main pieces of distributed computing since it conveys the fundamental advantages of distributed computing.
Be that as it may, virtualization in distributed computing carries a few dangers to information. One gamble is that a hypervisor could be hacked. If a hypervisor is feeble, it can turn into a principal target. In the event that a hypervisor is broken, the entire framework can be broken, and that implies that the information can likewise be broken. One more gamble of virtualization is how assets are given out and reclaimed. Chances and Answers For Information Security in Distributed computing On the off chance that VM activity information is kept in touch with memory and isn’t cleared before the memory is given to the following VM, the following VM could see the information, which probably won’t be what you need. Better anticipating the utilization of virtualization is one method for taking care of the issues above. Prior to opening up assets, they ought to be utilized cautiously, and information ought to be checked to ensure it is right.
- Storage in Public Cloud
Another potential security risk associated with cloud computing is the storing of data in a public cloud. Cloud computing typically makes use of centralized storage facilities, which might make them an attractive target for cybercriminals.
If there is even the slightest chance of a security breach in the public cloud, storage resources, which are complex systems consisting of a combination of hardware and software implementations, have the potential to expose sensitive data.
It is always advisable to have a private cloud for really sensitive data if one can get one if at all possible. This is so that such hazards can be avoided.
- Multitenancy
Chances and Answers For Information Security in Distributed computing One of the most significant threats to data in cloud computing is shared access, often known as multitenancy. When numerous users share the same CPU, storage, memory, etc., it poses a risk not just to one but to all of them.
A leak of sensitive information could occur in such a situation. It’s important to be cautious with multitenancy attacks because a single vulnerability can give an attacker access to all of the data in the system.
Carefully authenticating people before to granting them access to the data can prevent these kinds of problems. In order to prevent multitenancy problems in cloud computing, a number of authentication methods are in use
DATA SECURITY IN CLOUD COMPUTING
Chances and Answers For Information Security in Distributed computing Aside from encryption, the data connection is also crucial for cloud computing security. SaaS, PaaS, and IaaS are all different service models with varying requirements for protecting sensitive information.
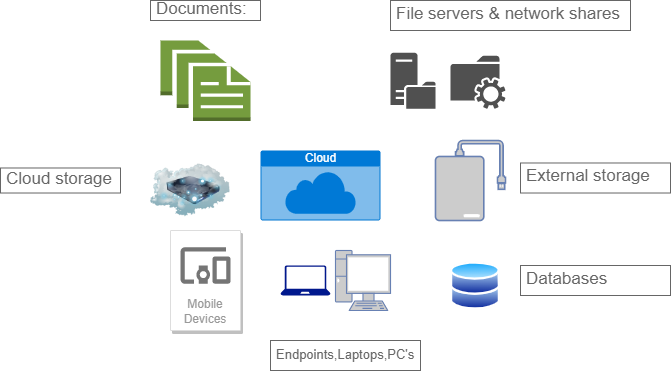
Chances and Answers For Information Security in Distributed computing Data at Rest, or information already in the cloud, Data in Transit, Data in Use, or information leaving the cloud, all pose risks to cloud security. The nature of data procedures, protection measures, and processes determines the data’s confidentiality and integrity. This is in three different forms.
- Data at Rest:-
The term “data at rest” refers to information that is stored in the cloud or any other data that may be accessed via the use of the internet. Chances and Answers For Information Security in Distributed computing This covers both active data and data that has been backed up. Because they do not have physical control over the data, businesses that do not keep their data in a private cloud can find it exceedingly difficult, as was said previously, to protect data while it is at rest if they do not have a private cloud. On the other hand, this problem can be overcome by preserving a private cloud that has access that is strictly regulated.
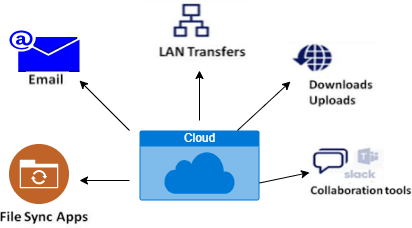
- Data Transit:-
The term “data in transit” is commonly used to describe information that is being uploaded or downloaded from a cloud storage service. One can request and use this information from another place, Chances and Answers For Information Security in Distributed computing as it can be saved in a file or database in the cloud. Data in transit refers to information that has not yet been fully stored in a cloud environment. Passwords and other login information are examples of very sensitive data that may require encryption while in transit. Unencrypted data is still data in transit, nevertheless.
- Data in Use:-
Data that is normally being used for processing, such as creation, change, or deletion. Due to the large number of users in the Cloud environment, the chances of mistreatment go up when processing takes place there.
MAJOR SECURITY CHALLENGES
Chances and Answers For Information Security in Distributed computing Because there are many computers and clients involved, it is not easy to secure and make sure the safety of computers that are linked. This is called “multi-tenancy.” Cloud service providers and cloud computing have to deal with a lot of problems, especially when it comes to security. So, it’s very important to think about how these challenges are simulated and how security models are put into place to keep clients safe and make cloud computing a safe place to work. The major challenges involved are :
1] Lack of appropriate governance:-
The cloud service provider continues to have full reign over the operation. When this authority is delegated to the provider, the client runs the risk of compromising data access and resource utilization due to a lack of oversight over the authorization parameters. In the absence of a Service Level Agreement between you and your service provider, this security risk poses the extra risk of leaving you vulnerable. Also, the user is given considerable leeway in how they put the terms of service to use, making it easier for data to be misused. You “accept that Google has no duty or liability for deletion or failure to preserve any material and other communication maintained or sent through use of the service,” according to Google’s terms of service. Further, Amazon makes it quite clear that they take no accountability for any harm caused by unauthorized access, usage, corruption, deletion of data, or other forms of intrusion into the program. As a result, consumers are put in a position where they must contemplate the security of their data and applications regardless of who hosts, provides, or mediates them.
2] Lock-in:-
Another problem is that there aren’t enough data format standards, there aren’t enough operating methods, and there aren’t enough tools. This makes it hard to move data between services and applications, even between service providers. So, the customer has to depend on the vendor completely and totally.
3] Isolation failure:-
The sharing of resources that arises as a result of the multi-tenancy feature of cloud computing is in and of itself a problematic quality. It might be disastrous for companies not to have adequate space for separate storage. Other concerns surrounding guest hopping attacks and the problems they cause are believed to be a significant obstacle in the utilization of cloud computing applications and their implementation.
4] Malicious attacks from management internally:-
There is a possibility that consumers’ privacy and security could be compromised due to the architecture of cloud computing systems in some cases. This danger presents a significant challenge, despite the fact that it only occasionally materialises. For instance, the administrators and managers of cloud service providers can occasionally pose a security risk to their customers by behaving in a malevolent manner and posing a threat to the clients that use cloud computing services.
5] Insecure or incomplete data deletion:-
When a client asks for some or all of their data to be deleted, it brings up the question of whether or not it will be possible to delete the right part of their data segment. This makes it harder for clients to sign up for cloud-computing services.
6] Data interception:-
In cloud computing, data is separated and dispersed while in transit, in contrast to traditional computing. This increases risks due to the insecurity and frailty of computer technology, especially with regards to sniffing and spoofing, third-party attacks, and reply assaults.
7] Compromise of management interface:-
Chances and Answers For Information Security in Distributed computing Since cloud services are provided remotely over the Internet and the provider has access to the resources, there is a risk of harmful actions being carried out. As a result, risks, service manipulation, and service provider involvement are all magnified.
For instance, in some cloud computing use cases, the client may assume ownership of the computers, while in others, the service provider may assume control by instituting strict access policies.
Information leakage during data uploading to the cloud, attacks on privacy and security of user’s data, lost or maliciously manipulated encryption keys, and disagreements between service providers and customers on procedures and policies pertaining to the operation of cloud computing applications all pose additional security challenges.
Chances and Answers For Information Security in Distributed computing Some complications don’t directly threaten the security of cloud applications but do interact with or influence cloud computing. Changes in network traffic, network outages, and managerial complications including inefficient resource utilization, traffic buildup, and lost connections all fall under this category. Social engineering assaults, natural disasters, and theft of equipment are just a few examples of additional threats that might impact cloud computing deployments.
PROPOSED SOLUTIONS/APPROACHES TO ENSURE THE DATA SECURITY IN THE CLOUD
1} Encryption:-
The most popular method for protecting information in the cloud was encryption (used by 45%). To protect cloud information, it is suggested using digital signatures based on the RSA method. Which program minimizes filesize by using a hashing algorithm? The digital signature is generated by encrypting the message digest using the individual’s private key in software. A digital signature is converted into a message digest by software using the recipient’s private key and the sender’s public key.
Use both the SDES and DES cypher methods for a more secure and robust game (DES). In this method, a 64-bit block of plain text is split in half using a “black box;” the right half contains two bits, while the left half contains six bits. These six bits are then fed into a “superior function” block, where they are split once again; the first two bits represent the rows, while the last four bits represent the columns. Then, the output from the vigenere block is multiplied by this function, which is applied to all eight octets. The output of the black box is 64 bits, which are subsequently subdivided into 4 new octaves. The left half is derived by XOR-ending the right and left halves. At least thrice
The data is encrypted using RSA, and the keys are securely exchanged using Bilinear Diffie-Hellman. The suggested solution adds a message header to each data packet so that clients can securely communicate with the cloud directly, without going through a proxy server. The server generates the user’s public key, private key, and user ID when the user requests cloud storage. To send data to the cloud, users must first encrypt their data using a private key and append a message header. The SID is looked for in the message header when a user makes a request to a cloud server. If the SID is located, the request is dealt with.
Secure Sockets Layer (SSL) 128-bit encryption, whichmay be upgraded to 256 bits, is introduced to guarantee the availability, integrity, and secrecy of cloud data. Access to encrypted cloud data requires a user ID and password. The user inputs data into the cloud, and the cloud service provider encrypts it with the RSA algorithm before storing it. The cloud service provider authenticates the user’s identity before handing over encrypted data that can be unlocked with a personal key.
The three layers of this data security approach all contribute to keeping cloud information safe. Data is authenticated in the first layer, encrypted in the second, and decrypted in the third. If your data is stored in the cloud, RC5 will keep it safe. Theft of encrypted data is catastrophic since no recovery key exists. With the help of role-based access control (RBAC) cloud architecture and the Role-Based Encryption (RBE) method, businesses can confidently store data in the public cloud while keeping sensitive information about their internal structures in a private cloud.
Information proprietor, information shopper, cloud server, and N characteristic specialists are the four characterized experts in. To send encoded information to a cloud server, the information’s proprietor should initially get a public key from the pertinent specialists. Subsequent to getting a solicitation for data, specialists create a confidential key and give it to the end client. Just once the client has been validated by the cloud administration can he download the document. There are two unmistakable ways to deal with safe distributed computing, one of which requires a solid outsider and the other of which doesn’t. Information put away in the cloud is safeguarded utilizing Elliptic Bend DiffieHellman (ECDH) and symmetric bivariate polynomial-based secret sharing.
In, an encryption technique reliant upon a client’s actual area was uncovered. Information was scrambled utilizing a geo encryption technique and marked with the firm or representative’s name in the cloud and on the client’s machine. Information is recovered utilizing a cloud-based look for a matching name at whatever point it is required. Data kept in the cloud can be encoded and marked carefully, as well as utilizing the Diffie-Hellman key trade and the High level Encryption Standard. The confirmation, information security, and check needs are met by this methodology.
2}Guidelines:-
According to the findings of research, 21% of studies use guidelines to guarantee the security of data stored in the cloud. By introducing a new cloud system architecture approach that has three features—separation of software service providers and infrastructure service providers, hiding information about the owner of the data, and data obfuscation—guidelines are provided for data security in the cloud in. In order to guarantee data security in cloud architecture, agents method is introduced. Data security was implemented using three agents: a file agent, an authentication agent, and a key managing agent.
Guidelines for six key data technologies are provided in, including those for protecting data privacy, proving the existence of data and making it usable, trusted access control, retrieving and processing cypher text, controlling access to cloud resources, and trusted cloud computing. In this book, guidelines are given along with a meta-analysis of four different encryption algorithms that can be used to help choose the best algorithm for a given situation.
3} Framework:-
Chances and Answers For Information Security in Distributed computing 14% of the results come from the framework approach. In Trust Cloud, a framework is given that uses a data-centric and detective approach to make data more secure. The goal is to encourage the use of file-centric and data-centric logging mechanisms to make data in cloud computing more secure and private. In, a framework is made by building a system with
multiple users. Chances and Answers For Information Security in Distributed computing The layers of a developed solution are the presentation layer, the business logic layer, and the data access layer. The data of users is very safe because of these layers.
Chances and Answers For Information Security in Distributed computing In, a framework is given that includes a protocol called Sec Cloud. Sec Cloud is a first protocol that covers secure storage and secure computation in a cloud environment through designated verifier signature, batch authentication, and probabilistic sampling procedures. In the proposed framework, there are three steps. In the first step, data and metadata are indexed to protect against cloud service providers that aren’t completely honest. In the second step, encrypted data is given a multi-user, private, keyword-searchable encryption to hide searches and the files that come from them from the cloud service provider. The last step is to use a policy to allow users to share data by using metadata and an encryption scheme.
4} Homomorphic Token:-
Chances and Answers For Information Security in Distributed computing 7% of the results come from the homomorphic token scheme. In this, a homomorphic token scheme is used to protect the security of the data. The proposed plan uses a homomorphic token and checks erasure-coded data in different places. It lets you delete, update, and add data to a data block safely and efficiently. By using a homomorphic token scheme with a token pre-computation algorithm, a model from achieves both storage correctness insurance and the identification of a server that is acting up (s).
5}Stripping algorithm, data concealment component, harmonizing, and token scheme:-
Chances and Answers For Information Security in Distributed computing The stripping algorithm, data concealment, and harmonizing and token scheme each contribute 3%. Stripping protects cloud photo data.The method has three parts: image analysis, data separation, and data distribution. Proposed a design for a data concealment component with three subcomponents: a prediction component, a data generator, and a data marking component, all of which would help keep cloud data safe. The evaluation of this part shows that legitimate users’ data is successfully hidden and that they are safe from possible attacks.
Chances and Answers For Information Security in Distributed computing A repository that protects privacy was shown in. This repository was mostly focused on harmonizing operations to keep data private while keeping harmonizing relationships in the cloud. With this plan, the owner of the data will be able to give most tasks that require a lot of computing power to cloud servers without revealing what the data is. To deal with data security in cloud computing, they came up with a good and flexible distribution verification protocol. This protocol checks the integrity of erasure-coded data instead of pseudorandom data by using token precomputation with a sobol sequence. The proposed model has three parts: the distribution of files, the pre-computing of tokens, and the challenge-response protocol.
CONCLUSIONS AND FUTURE DIRECTIONS
Chances and Answers For Information Security in Distributed computing Cloud computing is cost-effective, quick to deploy, and accessible. Many practical problems remain, though. One is data privacy. Many researchers contributed to this work to reduce data security issues in this domain. This paper presents a literature review on cloud computing data security. Future plans include exploring other cloud computing security issues and designing a data-concealment encryption model.
ACKNOWLEDGEMENT
I would like to express my very great appreciation to Prof Akanksha Kulkarni of ADYPU for her valuable and constructive suggestions during the planning and development of this research work.
REFERENCES:-
- J. Srinivas, K. Reddy, and A. Qyser, “Cloud Computing Basics,” Build. Infrastruct. Cloud Secur., vol. 1, no. September 2011, pp. 3–22, 2014.
- A. Vouk, “Cloud computing – Issues, research and implementations,” Proc. Int. Conf. Inf. Technol. Interfaces, ITI, pp. 31–40, 2008.
- S. Wooley, “Identifying Cloud Computing Security Risks,” Contin. Educ., vol. 1277, no. February, 2011.
- Alharthi, F. Yahya, R. J. Walters, and G. B. Wills, “An Overview of Cloud Services Adoption Challenges in Higher Education Institutions,” 2015.
- Subashini and V. Kavitha, “A survey on security issues in service delivery models of cloud computing,” J. Netw. Comput. Appl., vol. 34, no. 1, pp. 1–11, Jan. 2011.
- Zhang and H. Chen, “Security-Preserving Live Migration of Virtual Machines in the Cloud,” J. Netw. Syst. Manag., pp. 562–587, 2012.
- Hu and A. Klein, “A benchmark of transparent data encryption for migration of web applications in the cloud,” 8th IEEE Int. Symp. Dependable, Auton. Secur. Comput. DASC 2009, pp. 735–740, 2009.
- Descher, M., Masser, P., Feilhauer, T., Tjoa, A.M. and Huemer, “Retaining data control to the client in infrastructure clouds,” Int. Conf. Availability, Reliab. Secur. (pp. 9-16). IEEE., pp. pp. 9–16, 2009.
- Mohamed, “Enhanced data security model for cloud computing,” Informatics Syst. (INFOS), 2012 8th Int. Conf., pp. 12–17, 2012.
- Ajoudanian, Sh., and M. R. Ahmadi. “A Novel Data Security Model for Cloud Computing.” International Journal of Engineering and Technology, vol. 4, no. 3, IACSIT Press, 2012, pp. 326–29. .
- Kodada, Basappa B., and Demian Antony D’Mello. “Data Security Challenges in Cloud Computing.” Academia Letters, Academia.edu, July 2021
- Fakhruddin Noori , Abdul Ghafar “Omerkhel”, 2021, A Review on Data Security in Cloud Computing, INTERNATIONAL JOURNAL OF ENGINEERING RESEARCH & TECHNOLOGY (IJERT) Volume 10, Issue 03 (March 2021),
- Data Security in Cloud Computing by Ahmed Albugmi Madini O. Alassafi Robert Walters, Gary Wills
- Rachna, A., and Anshu, P.(Jul-Aug 2013). Secure User Data in Cloud Computing Using Encryption Algorithms in International Journal of Engineering Research and Applications (IJERA), 3(4),1922-
- Rachna, A., and Anshu, P.(Jul-Aug 2013). Secure User Data in Cloud Computing Using Encryption Algorithms in International Journal of Engineering Research and Applications (IJERA), 3(4),1922- 1926.
- Ko, R. K. L., Kirchberg, M., & Bu Sung, L. (2011, 3-5 Aug. 2011). From system-centric to data-centric logging Accountability, trust & security in cloud computing. Paper presented at the Defense Science Research Conference and Expo (DSR), 2011.
- Gawali, M. B., & Wagh, R. B. (2012, 6-8 Dec. 2012).
- Enhancement for data security in cloud computing environment. Paper presented at the Engineering (NUiCONE), 2012 Nirma University International Conference on.
- Wei, L., Zhu, H., Cao, Z., Dong, X., Jia, W., Chen, Y., et al. (2014). Security and privacy for storage and computation in cloud computing. Information Sciences, 258(0), 371-386.
- Rashid, F., Miri, A., & Woungang, I. (2013, June 28 2013-July 3 2013). Secure Enterprise Data Deduplication in the Cloud. Paper presented at the Cloud Computing (CLOUD), 2013 IEEE Sixth International Conference
- Cong, W., Qian, W., Kui, R., & Wenjing, L. (2009, 13-15 July 2009). Ensuring data storage security in Cloud Computing. Paper presented at the Quality of Service, 2009. IWQoS. 17th International Workshop on.
- Tribhuwan, M. R., Bhuyar, V. A., & Pirzade, S. (2010, 16-17 Oct. 2010). Ensuring Data Storage Security in Cloud Computing through Two-Way Handshake Based on Token Management. Paper presented at the Advances in Recent Technologies in Communication and Computing (ARTCom), 2010 International Conference
- Leistikow, R., & Tavangarian, D. (2013, 25-28 March 2013). Secure Picture Data Partitioning for Cloud Computing Services. Paper presented at the Advanced Information Networking and Applications Workshops (WAINA), 2013 27th International Conference
- Delettre, C., Boudaoud, K., & Riveill, M. (2011, June 28 2011- July 1 2011). Cloud computing, security and data concealment. Paper presented at the Computers and Communications (ISCC), 2011 IEEE Symposium on. [51] Mishra, R., Dash, S. K., Mishra, D. P., & Tripathy, A. (2011, 8- 10 April 2011). A privacy-preserving repository for securing data across the cloud. Paper presented at the Electronics Computer Technology (ICECT), 2011 3rd International Conference on.
- Syam Kumar, P., Subramanian, R., & Thamizh Selvam,
- (2010, 28-30 Oct. 2010). Ensuring data storage security in cloud computing using Sobol Sequence. Paper presented at the Parallel Distributed and Grid Computing (PDGC), 2010 1st International Conference on.
- Anane, R., Dhillon, S., & Bordbar, B. (2008). Stateless data concealment for distributed systems. Journal of Computer and System Sciences, 74(2), 243-254.
- An Efficient Approach on Data Security with Cloud Computing Environment: A Comprehensive Research Anjali Sharma1, Dr. Garima Sinha
- Turkish Journal of Computer and Mathematics Education Vol.12 No.14 (2021), 1372 – 1382
- International Journal of Advanced Research in Computer and Communication Engineering Vol. 10, Issue 7, July 2021 security in cloud computing Mitisha b Barot1, Prof.Riddhi Patel
- International Journal of Engineering Research & Technology (IJERT) ISSN: 2278-0181 Protection and Security of Data in Cloud Computing
- E. Poonguzhali
- Suhas Rao M V
- Shanth GK 4. Mujasem Khanum

