What is IAM?
AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources from unauthorized access. With Identity and Access Management (IAM), you can centrally manage the permissions that control which AWS resources users can access. You use IAM to control who is authenticated (connected) and authorized (has permissions) to use resources. Identity and Access Management (IAM) is a policy used by Amazon Web Service.
When you create an Amazon Web Service account, you start with a login identity that has full access to all AWS services and resources in the account. This identity is called the AWS account root user and is obtained by logging in with the email address and password you used to create the account.
We strongly recommend not using the root user to perform day-to-day tasks. Protect your root credentials and use them to perform tasks that only root users can perform. For a complete list of tasks that require you to log in as the root user, see Tasks Requiring Root User Credentials in the AWS Account Management Reference Guide.
IAM features

- AWS Identity and Access Management (IAM) Capabilities
IAM provides you with the following capabilities: - Shared Access to Your AWS Account
You can allow others to manage and use resources in your AWS account without sharing your passwords or access keys. - Fine-tuned permissions
For different resources, different permissions can be granted to different people. For example, you can grant certain users full access to Amazon Elastic Compute Cloud (Amazon EC2), Amazon Simple Storage Service (Amazon S3), Amazon DynamoDB, Amazon Redshift, and other AWS services. For other users, you can allow read-only access to only certain S3 buckets, or only allow management of certain EC2 instances, or access to your billing information, but nothing else. - Secure Access to AWS Resources for Applications Running on Amazon EC2
. You can use IAM features to securely provide credentials to applications running on EC2 instances.
These credentials allow your application to access other AWS resources. Examples include S3 buckets and DynamoDB tables. - Multi-Factor Authentication (MFA)
For added security, you can add two-factor authentication to your accounts and individual users. With MFA, you or your users must provide a password or access key to use your account and a code from a specially configured device. If you already use FIDO security keys with other services and the configuration is supported by AWS, you can use WebAuthn for MFA security.
For more information, see Supported configurations using FIDO security keys. - Identity Federation
You can allow users who already have passwords elsewhere (for example, on your corporate network or at an Internet identity provider) to gain temporary access to your AWS account. - Identity information for insurance
If you use AWS CloudTrail, you receive log records containing information about who requests resources in your account. This information is based on the IAM identity. - PCI DSS Compliance
AWS Identity and Access Management (IAM) enables merchants or service providers to process, store and transmit credit card data and is verified to be compliant with the Card Industry Data Security Standard (DSS). payment (PCI).
How it works
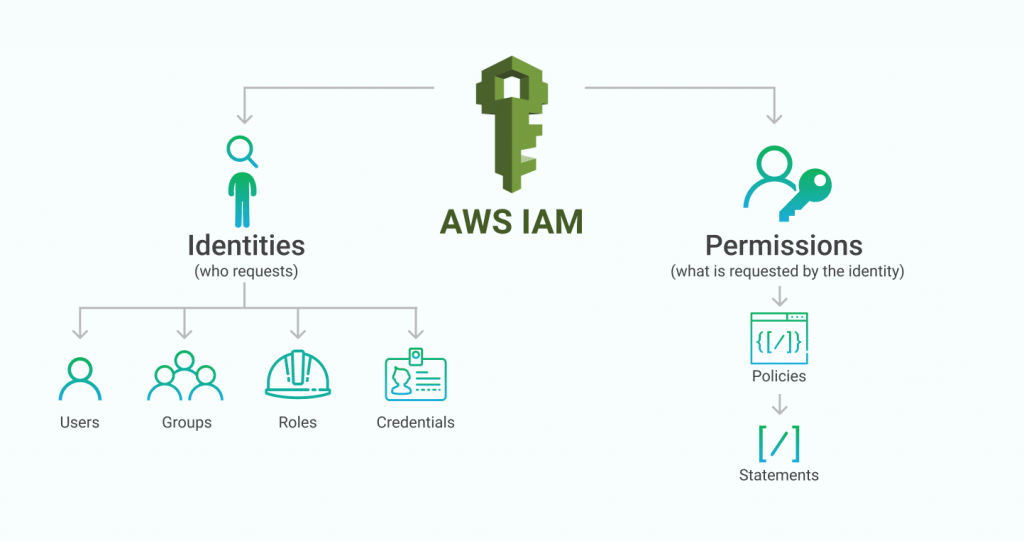
With AWS Identity and Access Management (IAM), you can specify who or what has access to services and resources in AWS, centrally manage granular permissions, and analyze access permissions to optimize permissions on AWS.
How to Implement Identity & Access Management (IAM) in 5 Easy Steps?
Step 1. Assess your current application technology landscape:
The first step is to review the different technology landscapes and information technology environments that your organization currently has.
To understand this, take an inventory of your current equipment, infrastructure, network, policy, and other regulatory details and ask yourself specific questions such as –
- What types of applications do your employees use?
- Which employees and groups require authentication to access organizational resources?
- What is your organization’s overall internal architecture and network infrastructure?
Step 2. Choose the right IAM solution for your needs:
Evaluating the right IAM solution is another critical factor that organizations must consider before choosing an IAM solution.
Factors such as security, compliance, cloud or on-premises, password, passwordless, risk-based authentication, multi-factor authentication, social login, phone login, and other authentication mechanisms come into play when choosing the right AWS Identity and Access Management (IAM) solution. Some of the well-known IAM products that organizations can choose from are Auth0, SailPoint, and Okta, among others.
Step 3. Defining Policies for an End-to-End IAM Solution:
Defining policies is essential when integrating IAM. Ensures that it reduces attack vectors and attack surfaces while enabling multiple layers of security. Having a strategy and vision in the mind of the CISO/CIO is the most effective step to implementing IAM in the organizational ecosystem. Implementing IAM with an appropriate strategy also requires dedicated stakeholder input and employee buy-in to make the IAM program fully functional.
Below is a list of strategies security professionals should consider when integrating IAM into their enterprise ecosystem.
- Determine business objectives and identify where IAM is required
- Determine cloud provider integration certification policy (CVOC)
- Define the deployment plan
Step #4. Transparent Implementation Plan:
Fundamental factors for a successful AWS Identity and Access Management (IAM) implementation include early employee and user engagement and training in the use of IAM with multi-factor authentication. In addition to enabling multi-factor authentication, IAM allows employees to use single sign-on, social login, phone login, smart login, and biometric login that organizations must enable.
Most IAM solutions come with AI and ML to intelligently detect external and internal threats and protect organizational resources from them.
Step #5. Continually Refine The AWS Identity and Access Management (IAM) Solution:
To do this, organizations must regularly rehearse and test the entire IAM solution they implement.
IAM providers should also require patch management plans and other updates as needed.
It is also important to ensure that the AWS Identity and Access Management (IAM) adheres to all compliance guidelines and the latest industry standard compliance policies published in the marketplace. A successful IAM program adapts to industry transformations and stakeholder perspectives.

